This is not a structural issue. It's a warning to others. I don't need any 'off topic' comments.
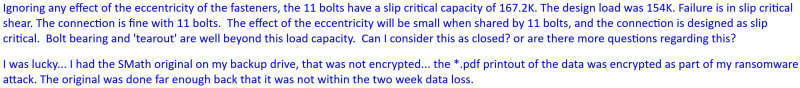
A couple of days back, I was hit by a ransomware virus that encrypted all my files, including the three backup drives that were attached to the computer. Fortunately I can recover nearly all my work (for the last 30 years) because I replaced my HDD with a new 16TB drive and had a full backup. This was just by accident that the loss wasn't much worse.
Future backups will include disconnecting backup drives from the computer when not in use as well as using some form of cloud storage.
I'm still working through it and still have to recreate some of my work. It's the dumbest, I've felt in years. Just a heads up... I'm pretty careful, but got 'hit'.
-----*****-----
So strange to see the singularity approaching while the entire planet is rapidly turning into a hellscape. -John Coates
-Dik
A couple of days back, I was hit by a ransomware virus that encrypted all my files, including the three backup drives that were attached to the computer. Fortunately I can recover nearly all my work (for the last 30 years) because I replaced my HDD with a new 16TB drive and had a full backup. This was just by accident that the loss wasn't much worse.
Future backups will include disconnecting backup drives from the computer when not in use as well as using some form of cloud storage.
I'm still working through it and still have to recreate some of my work. It's the dumbest, I've felt in years. Just a heads up... I'm pretty careful, but got 'hit'.
-----*****-----
So strange to see the singularity approaching while the entire planet is rapidly turning into a hellscape. -John Coates
-Dik